Introduction
COVID-19 has had a major impact on organisations across all sectors. While many organisations were unprepared, even organisations that had a strong culture of information security, privacy and business continuity, found it difficult to cope with the magnitude and unique nature of the disaster.
While COVID-19 will hopefully go away, we need to learn from our experiences during this crisis and adapt our practices especially in the domain of information security, privacy and business continuity. This is important as there is no way to predict such zoonotic outbreaks. COVID-19 has shown that several practices in these domains are quite brittle and hence do not naturally help us to respond to crises of this nature.
This article deals with the impact that COVID-19 has on the domains of information security, privacy and business continuity. It studies the impact of the crisis, how businesses coped with it from the perspective of information security, privacy and business continuity and finally suggestions on how these domains could evolve to meet future similar challenges.
Disruption caused by COVID-19
In many ways, COVID-19 was an unprecedented crisis. Some of its unique characteristics are:
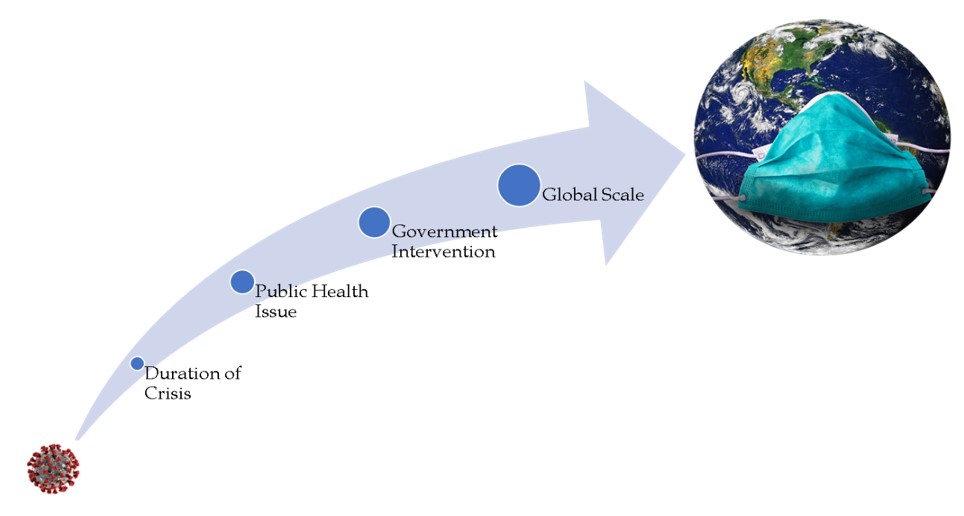 Duration of the crisis
Duration of the crisis
Initially most businesses thought the crisis would get over in a short period of time. However, as time went by, businesses realised that they are in it for the long haul. You could not just wait for the crisis to get over and then begin business. Hence businesses were forced to think of alternative ways of enabling staff to work.
Public Health Issue
The coronavirus was a public health issue that could affect anyone. More importantly it was very contagious and by making people to work with each other, organisations could put their entire workforce at risk. Hence organisations could not take chances with this pandemic.
Government Intervention
Given the severity, the government had to step in and impose almost draconian measures the curb the spread of the virus. This meant that organisations had little choice in the matter. When the government announced a lockdown, they were forced by law to shutdown irrespective of whether they felt that they could manage the coronavirus at their workplace or not.
Global Scale
The crisis was not a local crisis. It was a global crisis. Even global companies with global business continuity plans had not anticipated this level of disruption. At the highest level of business continuity planning, the strategy was to shift work to a different country. However, given the global scale of the crisis it quickly became apparent that this strategy would not work.
How did businesses cope
While essential services were allowed to continue, all other businesses were severely affected. However, various businesses were affected differently depending on the type of sector that they belonged to.
Businesses like manufacturing that were not and cannot be virtualized obviously could not continue.
The organizations that were largely digital with a mobile workforce having laptops and largely SaaS applications managed to quickly move to almost Business as Usual (BAU). This was a clear demonstration of the inbuilt resilience of using the Cloud rather than relying on “on-premise” applications.
Those businesses that were significantly virtualized (e.g. BFSI sector) could implement strategies like work from home. However, many of these businesses had either not planned for business continuity or had never planned for this level of disruption.
And then there were those businesses could have virtualized their activities, but never found it worthwhile to do so. For example, small professional services firms like CA firms and consulting firms. These small firms either never thought of this scenario or had not implemented measures like work from home due to security issues raised by clients.
To give you an example, one of our clients, a small professional services firm, that dealt in in financial services was expressly told by their clients never to keep their data on the cloud and disable any remote access of the data from home. However, when the lockdown kept extending, the very same clients demanded services and threatened to take their business elsewhere. Unfortunately, they lost many clients since they could not quickly get the infrastructure in place to enable remote access.
Now let us examine specifically how the domains of information security, privacy and business continuity were affected by COBID-19:
Information Security and Privacy
Information security is a multi -faceted domain. It includes not just logical security (e.g. technical controls like access control) but also physical controls (e.g. video surveillance, physical access control). During COVID-19, information security practices were tested and intensely scrutinized.
Let us examine some of the issues.
Organizations having on-premise systems with remote access provisions realized that they had not made provisions for the entire organization to work remotely. Their VPN servers did not have enough licenses and further having so many employees coming in remotely put a severe strain on the internet bandwidth.
Several organizations did not even provide laptops to their employees. Hence, they were forced to allow employees to access production systems using their personal devices with no clue of the security posture of these devices!
While many organizations managed to surmount this problem, a bigger issue emerged. While physical security controls (e.g. video surveillance) helped to keep data safe when employees were working from office, it was impossible to implement such controls when someone worked from home. Confidential information could be pilfered using various methods including taking photographs or even just writing it down on a piece of paper! Nothing an organization could do to prevent that.
Yet another deeper issue was that many organizations had never really implemented granular security controls to ensure that employees had access only on a “need basis”. For example, one BPO organization that processed of insurance policies for US clients allowed access to the Social Security Number to all employees processing such policies irrespective of whether they needed to access that data. Physical security controls were used to control the risk of data theft on site. However, now with employees working from home, since physical controls were absent, it became a major security risk. Organizations had not implemented controls to protect PII data of customers when this data was being accessed from home.
Another major challenge that confronted organizations was an increase of cyberattacks on end users. Relentless phishing, ransomware and business email compromise (BEC) attacks based on COVID-19 were launched. Organizations found themselves helpless to protect against such attacks given that many employees were working from home using personal devices and networks and were unaware of security measures required.
Business Continuity
If there is one domain that businesses really woke up to during COVID-19, it was the need for business continuity. There were two major impacts due to COVID-19 viz. non availability of premises due to the lockdown and non-availability of technology where organizations had not made provisions for employees to work remotely.
There were three major categories of companies based on their responses:
- Businesses that were unprepared: Some businesses had never planned for business continuity. Some probably heard of this term for the first time when the crisis struck. Some others had done business continuity just for “compliance” purposes. When the pandemic struck, they were left clutching paper-based business continuity plans that had never been tested and would never work. These businesses were hit hard and had to scramble to get things in place.
- Businesses that were not prepared for this intensity and duration of disaster: Several businesses had actually planned for business continuity, but the scale of COVID-19 stunned them. With its global impact, none of the plans worked out of the box. Organizations had to quickly customize and scale up their plans. However, the plans proved to be a boon since the strategy had already been pre-decided and tested. All they had to do was look for options to scale up their response.
- Businesses that were completely prepared: Several businesses were almost completely prepared for the crisis. Newer organizations that were “born digital” were able to quickly switch the entire organization to the remote working mode as they had all the necessary infrastructure in place.
Yet another major issue that organizations faced was that their Business Continuity Plans (BCPs) had never envisaged such a long and rapidly evolving crisis. Most BCPs cater only to critical processes and assume that since the crisis will be of a shorter duration, recovery of non-critical processes will not be required. How wrong that assumption was! Organizations had now to scramble to meet requirements of non-critical processes that became “critical” after some time.
Meeting the challenges
COVID-19 has certainly been a wakeup call for organizations. Even organizations having mature information security, privacy and business continuity practices were caught on the wrong foot. However, there are several lessons to be learned to meet similar challenges in future.
Information Security and Privacy
Information security is built on several key concepts like “Defence in depth”, “Least Privilege” etc. However, these concepts are not properly implemented and this gets highlighted during crises like COVID-19.
To illustrate this, let us study two examples along with some proposed solutions:
- Defence in depth: Most organizations trust connections to resources when they originate with their own office network. Access mechanisms are built around this assumption. However, during COVID-19, due to remote access requirements, this was not an easy task to accomplish given that users were accessing resources from the internet. Further, even access of Cloud applications from home meant that organizations had little control over security. This sort of access violated the “defence in depth” principle.Instead, companies could have implemented “Zero Trust” mechanisms that use defence in depth as its driving principle. Given the proliferation of Cloud solutions and blurring of the network perimeter, this “Trust but verify” approach would have helped organizations irrespective of whether employees were accessing resources from within the office or from home.
- Least Privilege: As mentioned earlier, employees had access to PII data fields that they did not need to, just by the virtue of physical controls being present at the place they worked from. Instead, organizations need to consider more granular application of the least privilege concept. Sensitive data like PII data must be identified and strict “least privilege” access should be implemented so that the data is only accessible to the right people irrespective of the location.
- Information Security Awareness: Another area that organizations realized needed more attention was information security awareness training. With employees working from an insecure IT environment, the only way organizations could remain secure was by empowering employees through training.
Business Continuity
For Business Continuity practitioners, COVID-19 was a trial by fire. Given the duration and intensity of the crisis, most Business Continuity Plans were found to be inadequate. Organizations had to quickly improvise to meet business demands. Some of the key learnings that we can take away from this are:
- Business Continuity Plans should cater to both critical and non-critical activities. As we know, even non-critical activities become critical after a certain period
- Pandemic plans are a vital part of business continuity and must be created
- Organizations need to think about IT “Resilience” rather than IT Disaster Recovery. What that means is that organizations must embrace technologies like the Cloud and mobile computing resources like laptops to ensure that they have the flexibility to move the workforce around
- Plans must be practical and tested rather than be created for compliance or certification purposes!
Conclusions
COVID-19 has certainly been a wake-up call for information security, privacy and business continuity professionals. The unique nature of this crisis has raised several questions that must be answered so that such crises could be better handled in future.
While information security concepts do exist that can meet the challenges posed by COVID-19, organizations need to re-examine their implementation of controls and ensure that the controls implemented can provide defence in depth. With personal data coming under increasing threat and scrutiny, it is important that organizations identify and protect the data in ways that keep it secure irrespective of location of access.
Finally, business continuity as a practice needs to further evolve to take into consideration long duration crises. IT Disaster recovery needs to consider not just recovery but the larger goal of resilience.
About the author:
Keith Prabhu (CISA, CISSP, CCSP, CCSK, MBCI and ISO27001 Lead Implementer) is the Founder & CEO, Confidis (www.confidis.co). He has over 2 decades of experience in areas of Information Security, Privacy and Business Continuity. He has previously worked with KPMG, Deloitte, HSBC Software, Arthur Andersen and HCL Infosystems. He volunteers with the Centre of Social Action, an NGO that works with vulnerable children and women’s empowerment.
(Note: This article first appeared in the ISACA Mumbai Chapter Magazine, July 2020)
