India is among the top 5 countries in the world to be affected by ransomware. This actionable security advisory aims to provide information about ransomware and ways to counter this threat.
What is ransomware?
In layperson’s terms, ransomware is someone locking up your door with their lock and demanding a ransom from you to provide the key.
Technically, ransomware is malicious software (malware) that seeks to 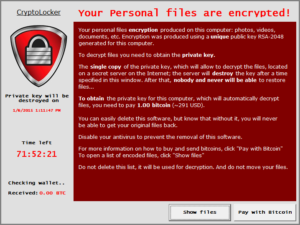 elicit a ransom payment from a victim. When ransomware infects a system it commonly encrypts all of the document files on the hard drive as well as accessible network folders. Documents so encrypted are unusable unless decrypted with a unique decryption key held by the attackers.
elicit a ransom payment from a victim. When ransomware infects a system it commonly encrypts all of the document files on the hard drive as well as accessible network folders. Documents so encrypted are unusable unless decrypted with a unique decryption key held by the attackers.
After a ransomware infection takes hold, instructions on how to pay the ransom are presented, typically demanding payment in the virtual currency known as Bitcoin to obtain the decryption key.
How can a system become infected with ransomware?
Ransomware infections typically occur by opening malicious attachments and links in spam/phishing emails and by browsing to a website that’s been compromised to infect visitors. Systems infected with other forms of malware can also be commanded by attackers to retrieve and install ransomware.
Can ransomware spread from one computer to another?
Yes. Ransomware is becoming contagious. A recent ransomware version additionally attempts to infect other computers and transform affected document files into infectious ransomware programs. An uninfected system can become infected when such a document is opened. In this way, ransomware infections can spread across systems that access a common shared folder, for example.
Does security (anti-virus) software protect against ransomware?
Anti-virus software detects and prevents infection from known ransomware variants, but there can be a period between the release of a new ransomware variant and effective anti-virus protection. Running up-to-date anti-virus software is important but protection is not absolute. Security software that includes an intrusion prevention feature can also help to prevent ransomware from spreading between systems.
I have been hit by ransomware. Can I hope to recover without paying ransom?
Given the strength of the lock used (encryption) it would take months and maybe years—to decrypt. In case you have been hit by an older versions of ransomware, you may just get lucky. Some of the older ransomware have fatal flaws in them in which they store the decryption key in memory or on the hard drive.
Should I pay?
Paying a ransom does not guarantee an organization will regain access to their data. In fact, some individuals or organizations were never provided with decryption keys after paying a ransom. Recent cases have come to light where ransomware deletes all files on infection and no files are recoverable even after payment of ransom.
Paying a ransom emboldens the adversary to target other organizations for profit and provides a lucrative environment for other criminals to become involved. While we do not advocate paying a ransom, there is an understanding that when businesses are faced with an inability to function, executives will evaluate all options to protect their shareholders, employees, and customers.
How can I avoid getting hit by ransomware?
Like every other cyber threat, while you can never totally eliminate the threat, you can significantly reduce the chances of getting affected by following some simple steps:
Action to be taken by users of computer systems
- Be wary and skeptical of unsolicited email that demands immediate action even from well-known and reputable companies or government agencies, including well-designed but counterfeit invoices and failed courier delivery notices or claims of illegal activity
- Don’t click on links or attachments in email from unfamiliar sources or that seem suspicious—call the source to confirm authenticity
- Maintain up-to-date security (anti-virus) software
- Practice safe online behavior
- Avoid visiting porn sites, pirate sites, downloading pirated software and other media
Action to be taken by CIO/CISO
- Awareness: Ransomware, along with most other malware solutions, rely heavily on the average end-user’s lack of technical knowledge to facilitate their infiltration and execution. Arming personnel with critical knowledge, as well as implementing corporate policy governing web-surfing and email procedures may reduce the chances of a phishing scam or drive-by download being successful. Be sure to provide basic end-user awareness training regarding typical phishing e-mail campaigns and the “do’s and don’ts” of general web-surfing and corporate email
- Backup, verify :All important documents and files must be backed up on a regular, ongoing basis. Don’t just backup, verify your backups to ensure that they can indeed be restored when required. Ensure backups are not connected to the computers and networks they are backing up. Remember that replication of your data to a remote system or the cloud is not the same as taking offline backups. There have been cases where ransomware has managed to infect both the primary and secondary servers. Backups are critical in ransomware; if you are infected, backups may be the best way to recover your critical data
- Email filtering: Be vigilant and aggressive in blocking file extensions via email. While blocking *.js, *.wsf, or scanning the contents of *.zip files may be in place as basic filtering functions, there remain further avenues to explore. Consider screening and filtering *.zip files outright if there is no business requirement to allow them
- Segmentation: Categorize data based on organizational value, and implement physical/logical separation of networks and data for different organization units. For example, sensitive research or business data should not reside on the same server and/or network segment as an organization’s e-mail environment
- Additional authentication for risky websites: Require user interaction for end user applications communicating with websites uncategorized by the network proxy or firewall. Examples include requiring users to type information or enter a password when their system communicates with a website uncategorized by the proxy or firewall
- Workstation protection
- Install ad-blockers and script-blockers as standard programs for all workstations. Drive-by malware is increasing exponentially and is extremely prominent in today’s technology ecosystem. Blocker solutions help to cut off this vector of infection
- Implement application whitelisting. Only allow systems to execute programs known and permitted by security policy
- Use virtualized environments to execute operating system environments or specific programs
- Patch the operating system, software, and firmware on devices. All endpoints should be patched as vulnerabilities are discovered. This can be made easier through a centralized patch management system
- Ensure anti-virus and anti-malware solutions are set to automatically update and regular scans are conducted
- Manage the use of privileged accounts. Implement the principle of least privilege. No users should be assigned administrative access unless absolutely needed. Those with a need for administrator accounts should only use them when necessary; and they should operate with standard user accounts at all other times
- Implement least privilege for file, directory, and network share permissions. If a user only needs to read specific files, they should not have write access to those files, directories, or shares. Configure access controls with least privilege in mind
- Disable macro scripts from office files transmitted via e-mail. Consider using Office Viewer software to open Microsoft Office files transmitted via e-mail instead of full office suite applications
- Implement software restriction policies (SRP) or other controls to prevent the execution of programs in common ransomware locations, such as temporary folders supporting popular Internet browsers, or compression/decompression programs, including those located in the AppData/LocalAppData folder
Sources: FBI Circular on ransomware, City University of New York advisory on ransomware
About Confidis
Confidis works at the intersection of business and technology. We provide advisory services in security, continuity and technology. Our extensive experience in providing management consulting services in various domains including strategy, operations, Information Technology, security, and training enables us to provide innovative ways of developing people, skills and business that can make a difference to you and your company. We believe in having our “skin in the game”. Hence, our services extend beyond providing merely advice to management. We are prepared to implement the advice we give.
Disclaimer
Confidis refers to Confidis Advisory Services Private Limited. This material is prepared by Confidis. This material (including any information contained in it) is intended to provide general information on a particular subject(s) and is not an exhaustive treatment of such subject(s) or a substitute to obtaining professional services or advice. This material may contain information sourced from publicly available information or other third party sources. Confidis does not independently verify any such sources and is not responsible for any loss whatsoever caused due to reliance placed on information sourced from such sources. Confidis, by means of this material, is not rendering any kind of professional advice or services.
You should seek specific advice of the relevant professional(s) for these kind of services. This material or information is not intended to be relied upon as the sole basis for any decision which may affect you or your business. Before making any decision or taking any action that might affect your personal finances or business, you should consult a qualified professional adviser.
Confidis shall not be responsible for any loss whatsoever sustained by any person or entity by reason of access to, use of or reliance on, this material. By using this material or any information contained in it, the user accepts this entire notice and terms of use.
©2016 Confidis Advisory Services Private Limited
